Web browsers sure have come a long way, and today we have the privilege of being able to select from several competing brands. The more competition there is, the better the quality of the browsers.
It doesn’t seem like that long ago that Microsoft’s Internet Explorer was the de facto web browser of choice, mainly because browser technologies hadn’t exploded as they have today.
Fortunately, users can select their browser of choice from options such as Firefox, IE, Opera, Safari, Google Chrome, Epic Privacy Browser, Comdo Dragon, Tor, Dooble, Maxthon, and a myriad of other options that you likely haven’t heard of before. But realize that not all web browsers were created equal.
Even though it’s common for mainstream browsers like Firefox and Chrome to include plugin and add-on functionality to enhance browser features, most mainstream web browsers are not secure by default.
Why Use a Private Browser?
Despite their security flaws, traditional web browsers like Firefox, Chrome, and IE are not dead. In fact, with a certain degree of configuration, they can be just as secure as the top private browsers.
Just about every web browser that’s worth its salt has a privacy mode these days, which enhances security by refraining from storing browsing data, cookies, history, and other data.
Furthermore, you can add extra security features via addons. For instance, if you wanted to stop cookie storage dead in its tracks and prevent targeted online advertising, all you’d need to do is download and install the right plugins.
But since standard browsers can be configured to be drastically more safe and private, that begs the question: why use a private browser at all?
Well, there are several reasons. First of all, the guiding principle behind making a browser secure is to streamline the software by removing every unnecessary feature to make the browser as ‘bare-bones’ as possible.
This provides several key advantages. First of all, limiting the features of the browser increases performance, page load times, and decreases the amount of CPU cycles and memory used by the browser.
Secondly, private browsers don’t suffer from fingerprinting as much as their alternatives. But what is fingerprinting, you ask? Well, web browsers are like fingerprints or snowflakes, in that no two are exactly the same (with exception to fresh, new installs).
Whenever a browser makes a connection to a web server, it’s possible for the web server to collect information such as web browser type, version, OS version, installed addons, and a plethora of other identifying information that the average user doesn’t think about.
All of these minute differences, when added together, can uniquely identify a browser. That is, it’s so incredibly unlikely that someone else has their web browser setup exactly like yours, because there are too many unique variables.
This makes it possible to track online activities based on a browser’s unique fingerprint identity. Fortunately, private browsers, being stripped of all the extra unnecessary functionality, don’t fall victim to fingerprinting as easily as standard alternatives.
Thirdly, because private browsers are streamlined, they don’t leave the door open for nearly as many attacks as standard browsers.
For instance, plugins like Flash video and active-x are notorious for giving attackers a foothold where they can run malicious scripts. Private browsers don’t have all these extra addons, so there is a highly reduced threat of vulnerabilities.
Privacy Tip: Private Browsers Are Only One Part of the Security Equation
Using one of the best private browsers is only one component of a successful security strategy, however. While you should use one of the best private browsers to protect your online security and anonymity, there are several other things you need to do to drastically enhance your online protection.
More specifically, you should use 3 other main tools: VPNs, private search engines, and ad blocking software.
VPNs, or Virtual Private Networks, will increase security by adding encryption to your Internet connection. Encrypted data is impossible for ISPs, governmental agencies, and hackers to read, Furthermore, the VPN server obfuscates the source of your data by masking your IP address.
Masking makes it nigh on impossible for online entities to track your browsing habits, since your real IP address isn’t used outside the scope of the connection to the VPN server.
Private search engines should also be used in conjunction with private browsers and VPN tunnels.
Most people aren’t aware that Google (among other leading search engines) stores and tracks a lot of personal information, and is sophisticated enough to learn which websites you visit the most in order to send you targeted ads. There are many private search engines available, but I prefer DuckDuckGo.
Lastly, you should also use ad blocking software to increase privacy and anonymity. Though the aforementioned services will help stop targeted online advertising, you should still use an ad block religously.
Not only will it speed up your Internet connection by saving bandwidth that would have otherwise been used to load images for popup windows, but it will also help you manage cookies. Cookies have been used as a way to track users for years now, but ad blocking software will help limit, delete, and manage cookies.
With that said, let’s go ahead and take a look at the best private browsers.
The Epic Privacy Browser
Epic is our first pick as the best private browser, and it is a prime example of an ultra-streamlined web utility that has removed the vast majority of features to bolster anonymity and security. The look and feel of the interface and buttons mirrors Google Chrome and Firefox, so it won’t feel alien to use.
After each browsing session, it will automatically delete tracking data and cookies, and they even send search queries through their own servers to strip off tracking data that could be collected by Google.
Naturally, Epic doesn’t collect any user data (even in an anonymous fashion) like other services do, and it even comes with ad blocking features right out of the box.
And though it doesn’t come with addons by default, there are some useful security extensions such as encrypted password managers. The only thing I didn’t like about it is that it lacks antimalware features, but you can (and should) use a stand-alone antimalware app on your host system.
Comodo Dragon Secure Browser
Comdo Dragon is a long time creator and developer of security tools, such as their free firewall solution. To date they run two different forks of their secure browser; namely Dragon (the Chromium version) and Ice Dragon (which heavily resembles Firefox).
Each separate version strives to create compatibility with features, plugins, passwords, and bookmark data of its browser counterpart.
Interestingly enough, Comodo includes a Secure DNS feature that can be configured for use via their browser alone, or for all apps on a local system. This will shield your data and web requests from visibility by your ISP. Furthermore, they include a list of malicious websites to stop you from visiting a dubious domain.
I also found it interesting that they have a feature to virtualize the browser, which separates it from the host OS. The separation will help prevent the spread of viruses should you download a bad file.
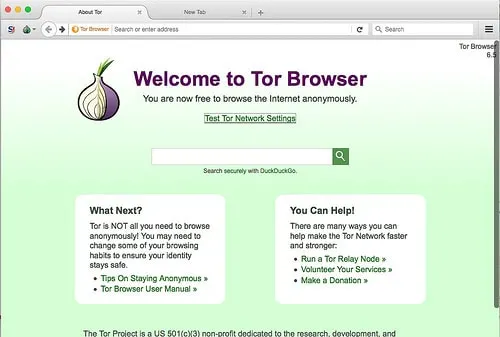
The Tor Browser
This list couldn’t possibly be complete without mentioning the Tor browser and the Tor anonymity network. You have likely already heard how the Tor network bounces your data around through a network of private relay servers to make it nearly impossible to trace the origin of the data.
However, keep in mind that the Tor browser excels at privacy, and not security. You see, it doesn’t include any antimalware or antivirus services, and intentionally prevents plugins from being installed.
Nevertheless, it does inform users of best practices, such as adhering to only HTTPS connections and refraining from opening files and data that necessitate using external apps.
And keep in mind that there are trade-offs with using the Tor browser. Because your data gets sent through several hops of relay servers before being forwarded to the correct destination, you can expect a slightly slower connection.
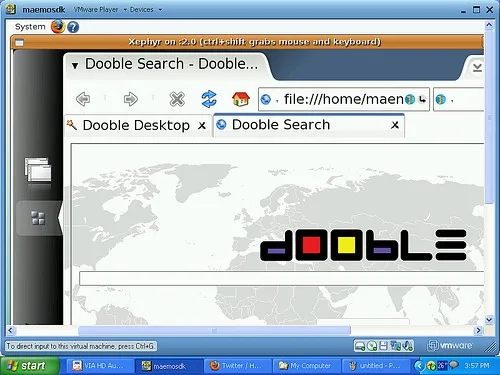
Dooble
Dooble may have a silly name, but it’s a serious privacy tool. It’s based on Chromium, and will run in Windows, Linux, and OSX – so all the major bases are covered. It was designed to be light and lean to enhance security, and by default it doesn’t run Flash or Javascript since they are notoriously insecure.
That means that it will be difficult to browse through most of the web, however, since Javascript and Flash are so ubiquitous.
Furthermore, it won’t store cookies or load iFrames by default, either. Interestingly enough, they even chose to lock down users’ personal content, such as bookmarks, cached passwords, history, and other similar data with encryption using a master password.
And if you want to enable private browsing mode on the fly, all you need to do is right-click to open a new tab. Dooble isn’t incredibly popular, though, because a lot of people feel that they stripped it down so much that it’s nearly unusable. But I digress; it’s a great privacy tool and one of the best private browsers.
Maxthon
Last but not least, we have Maxthon, which is another solution compatible with HTML5. This browser is a bit odd, however, because it has it’s development roots in China, and was originally created to bridge the gap between mobile and desktop synchronization.
It’s actually pretty different from traditional browsers, and is called a ‘cloud browser.’ I did really like how it includes AdBlock protection so you’re not inundated with annoying pop-ups. And any files that are synced to the cloud are automatically encrypted with AES-256.
Nevertheless, it seems that their focus is on cloud integration rather than security, though they are more secure than a traditional browser.
Final Thoughts
Using a private browser is only one component of a strong Internet security profile. There are several things I would recommend in addition to using one of the aforementioned browsers as follows:
- Use an anonymity network in conjunction with encryption (such as Tor (link to website))
- Don’t cache usernames or passwords in your browser – instead, use an encrypted password manager like KeePass or Lastpass (Check out how they compare)
- Always use a VPN tunnel if it’s possible
- If your really want to beef up security and anonymity, try out a Linux distribution like TAILS, JonDo, Whonix, or other similar operating systems on a live flash drive
- Stay away from most Google services and insecure cloud storage services like Dropbox
- Use adblockers regardless of which browser you choose
- Use antivirus software religiously (see my review)
The web is a scary place these days, and it’s truly frightening how much information people can collect about you. But by following these best practices, you will drastically reduce the risk of being victimized by an attack or being spied on.




anon
Sunday 5th of November 2017
TOR Is no longer private the NSA/CIA can unanonymize TOR users through exit nodes easily. That and epic browser is also not a good option either. So we're screwed. Privacy and anonymity are all fake. Nothing is private it's just slightly more difficult and annoying for them to hack into. VPN users are now targets for the CIA/NSA and FBI they're now seen as criminals. Anyone who uses a VPN are criminals according to the US government. Look it up there's articles on it.