There always seems to be a lot of misinformation floating around on the Internet, and this couldn’t be truer than it is for the classic debate between VPN tunnels and SSH tunnels. The fact is that VPNs don’t provide the only means of encryption.
Believe it or not, every time you connect to a web server and see the little padlock in the URL pane of your web browser, you are, in fact, using a type of encryption known as HTTPS. So if there are so many types of encryption available, why use a VPN tunnel in the first place?
Well, there are several advantages to VPN tunnels that surpass raw encryption. However, we first need to look at the SSH protocol, understand what is, and how it protects data. Then we’ll take a closer look at VPN encryption technologies. Believe it or not, there are some very clever ways to disguise your VPN tunnel to add an extra layer of protection.
But first, let’s dig into the history, functionality, and security benefits of SSH.
SSH History
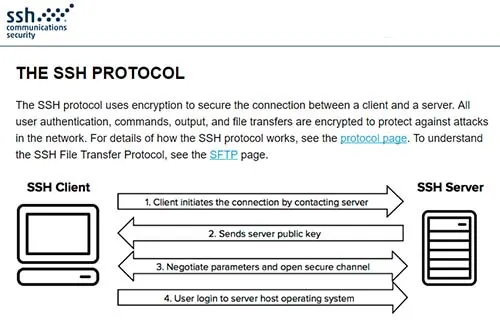
SSH, a protocol whose acronym stands for Secure SHell, offers another form of encryption. When it was first created, it was designed to be a secure alternative to Telnet. Both Telnet and SSH were originally used to log in remotely to servers and networking equipment, whereby an administrator or network engineer would enter in text via a command line interface.
The drawback to Telnet was that it would send commands (even usernames and passwords!) in plain text. That made it very easy for hackers and eavesdroppers to steal login credentials with packet sniffers.
The security drawbacks of Telnet were so immense that the demand for encryption surfaced, and SSH was born. The first version of SSH (SSH-1) was created at the Helsinki University of Technology in Finland by a researcher named Tatu Ylönen in 1995. It worked tremendously well and overcame the shortcomings of Telnet and other similar protocols.
Over the next couple of decades, SSH grew in popularity and complexity. The latest version, SSH-2, improved upon the older standard and is defined in RFC 4251. It is among the most commonly used Internet protocols to encrypt data. If that’s the case, can’t you just use SSH in lieu of a VPN tunnel? Well, not exactly.
SSH at a Glance
Some people have even called SSH the “poor man’s VPN.” And it can certainly be leveraged to bolster online security, but it lacks many of the advantages of a true VPN tunnel. For example, let’s consider how the tunnels and sessions are created.
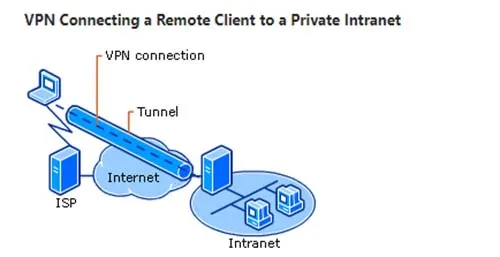
With a VPN tunnel, you are able to create a secure connection to a VPN server, thereby encrypting all communications with remote hosts on the remote LAN where the VPN server is located. On the other hand, SSH only creates a secure tunnel with one endpoint device who will then forward your messages to other destinations.
In technical terms, this is known as unicast, whereby the communication only happens between two endpoint devices.
VPN Tunnels in Depth
There are several differences between SSH and VPN tunnels, the largest of which is how they work within the OSI model. You see, VPNs function as a transport protocol, while SSH works at the application level. This means that VPNs can act more like a network utility designed to support higher level functions and applications while SSH doesn’t support higher level protocols and traffic.
Whether you use a site-to-site or endpoint VPN, all of the application traffic is routed through the encrypted tunnel (unless otherwise configured or specified). That said, both SSH and VPN tunnels can be used to provide similar levels of security by means of encryption. If either SSH or VPN traffic is intercepted during transit, there’s nothing a hacker can do to read the data without the encryption key.
Also, VPNs are typically much easier to configure. However, one drawback is that there are many competing VPN technologies, while SSH really only has one viable standard. Generally speaking, SSH usually requires much less support and configuration that VPN tunnels since it is simpler and only adheres to one standard.
While this may be true, also understand that all the competent VPN services are more than well-equipped with 24/7 customer support.
VPN Pros:
- Can disguise network traffic by routing protocols to different ports
- Can use either TCP or UDP connections
- More flexible routing options
VPN Cons:
- Requires more support
- There isn’t a single, overarching, unified standard
- Usually cost money
SSH in Depth
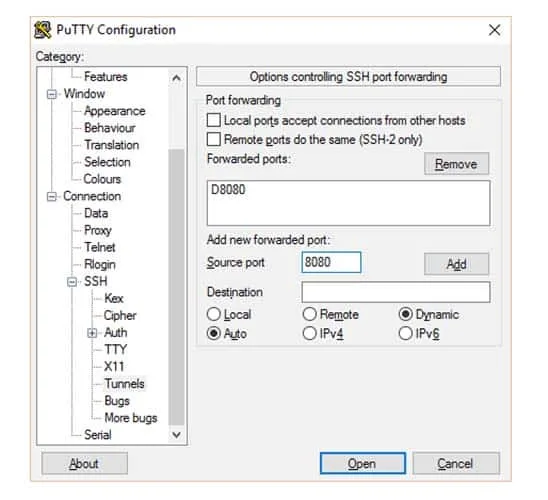
As stated previously, SSH works at the application level of the OSI model. Before it can provide the benefits of encryption and security, a session must first be configured and established using a computer program or app. One of the most popular applications used for creating SSH tunnels is PuTTY, which can be downloaded completely free of charge.
Also take note that SSH does not encrypt all of your data and traffic. Rather, it only encrypts data sent through the application. For example, if you used PuTTY to establish a remote connection to a server or networking device, then only the commands sent through the PuTTY terminal window will be encrypted.
This is undesirable for people who want to encrypt all communications to evade censorship laws, geo-restricted connections, and wiretapping by ISPs and governmental institutions. In this case, SSH is severely limited in the scope of encryption it can provide for your Internet transmissions.
On the other hand, the failure to encrypt all data could be seen in a good light since encryption adds overhead to Internet connections. One drawback, however, is that it is much more difficult to disguise SSH traffic as another type of protocol.
And to use it for encryption on a practical scale, a user would first need to setup and configure each connection individually and configure the use of a SOCKS proxy server.
SSH Pros:
- Can be run free of charge
- Single standard
SSH Cons:
- Application level protocol that won’t encrypt all data communications
- Can be challenging to setup for novices
- Cannot use UDP
- Harder to hide traffic and make it look like something other than SSH
- DNS leaks are more prevalent
If there’s more drawbacks to SSH as opposed to VPN tunnels – at least from a privacy and security standpoint – then is there any value to SSH? Of course there is. For users concerned with encrypting their traffic to make it secure from hackers, ISPs, and governments, I would recommend using a VPN tunnel at the very least.
However, there’s a handy trick you can use to disguise VPN traffic as SSH traffic, as we’ll discuss next.
Using SSH to Hide VPN Traffic
In some corners of the world, Internet censorship is at an all-time high, and governments are cracking down on the use of VPN tunnels used as a means for private communications and workarounds to governmentally imposed Internet filtering programs.
The worst offender might very well be China and the well-named Great Firewall of China (GFW) – but there are users in other areas such as the Middle East and Southeast Asia that suffer from the same problems.
Though it is rare, some networks in the United States may even block VPN tunnels to prevent the circumvention of network restrictions (like school campuses, some local work environments, etc.). The cat is out of the bag, and many organizations want to prevent people from using a VPN tunnel to access restricted content for a variety of reasons.
Furthermore, some people just want to be as private as possible by laying low. In these cases, it is highly advantageous to disguise VPN traffic as another type of protocol. While there are several methods of hiding VNP traffic, one of the most common methods is to make it look like SSH traffic.
Even though it is impossible for an external party to view the contents of encrypted VPN data, some firewalls use DPI (Deep Packet Inspection) to identify specific protocols. And some might even apply rate limiting techniques on certain ports to cap data limits for VPN users.
Just about every method of circumventing these problems requires two things: a certain degree of technical knowledge as well as a configuration on the VPN server. For users who run their own home-made VPN servers, this won’t be an issue.
But for users who use a VPN service, you’ll need to contact customer support and ask them to help make a configuration for your account. Some will and some won’t – it just depends on their policy.
One of the few exceptions is AirVPN, which supports SSH tunneling from the get-go. Remember, however, that you won’t otherwise have the ability to tunnel a VPN through SSH unless you can create a server-side configuration.
Since you don’t have access to the server, your VPN provider is going to need to help you out. Most will accommodate their customers, and it’s not a big problem to tunnel VPN traffic over a different port. However, you’re going to want to open a support ticket or call the customer support department.
In Summary
Though it often isn’t necessary to disguise a VPN as SSH, some people want to take every precaution to be as clandestine and anonymous on the Internet as humanly possible. You should have a good understanding of the differences between VPNs and SSH.
Remember that SSH, in and of itself, is not really a viable substitute for VPNs – and anyone who tells you different is dead wrong. Though SSH does provide and encrypted tunnel between two endpoints, it really doesn’t come close to offering the functionality and security of a VPN.