Most people who use Bittorrent on a regular or even semi-regular basis understand that it is a P2P (peer-to-peer) technology, but what exactly does that mean? And what’s the difference between Bittorrent P2P downloads and other download methods, such as traditional file hosting or services
like Usenet?
Bittorrent traffic is still an alarmingly high percentage of total data transmitted in the US, and it doesn’t seem that things are slowing down. Despite outcries from copyright agencies and the RIAA, people are still sharing files like crazy.
I’m sure many of you remember the days of Napster, Kazaa, and LimeWire. Even though these P2P services were ultimately shut down, the authorities are having similar difficulties shutting down BitTorrent and P2P technologies as they would playing a game of whack-a-mole – there’s always a new torrent portal popping up.
And though The Pirate Bay has met its share of challenges, it seems to be immortal. Even if it’s blocked in any given geographic location, users turn to VPN tunnels to access the blocked content.
The bottom line is that P2P technologies don’t look like they’re going to disappear anytime soon, though you should also note that BitTorrent isn’t an inherently evil tool. Though it can be used to share just about any file you can think of, it isn’t used exclusively to share copyrighted content.
Instead, it’s frequently used as a distribution medium for free and legal software too, such as applications protected under the GNU license. For instance, plenty of Linux distributions are distributed via torrents.
But even seemingly innocuous downloads from sources that look trustworthy still introduce a certain amount of risk. The problem with P2P technologies is that your computer makes tens, if not hundreds, of connections to strangers’ computers.
And you never know if there’s a bad apple in your download swarm, just waiting to launch an attack and exploit your computer. But before we talk about the inherent risks of downloading files via Bittorrent and how to mitigate them, let’s first talk about the differences between traditional file downloads
and P2P.
Traditional File Downloads and Usenet
Whenever you download a file without using P2P technologies, your computer is typically only making a connection to a single server.
Basically, there is only one TCP/IP session between your computer’s network interface and the server’s. In addition, consider that the bulk of the data (with exception of protocol overhead and metadata) only flows in one direction: from the server to your computer.
The server hosting the file is typically tied to a single domain or URL, too. This makes it a lot easier to verify the source of the data, and you can be reasonably sure that the server hosting the file
is trustworthy.
Untrustworthy domains, such as those that distribute viruses and malware, are usually flagged or blacklisted pretty quickly. In turn, antimalware and security applications throw a warning if you’re about to visit a dangerous site.
Since there’s only one server hosting the file, you can be more or less confident that your download won’t endanger your personal data, computer hardware, or identity. And Usenet, which is commonly seen as a competing technology with BitTorrent, uses a similar distribution model as
traditional downloads.
Users have to pay Usenet for access to files that are hosted on decentralized networks of servers. Alternatively, note that BitTorrent users are downloading files directly off the hard drives of their peers. As such, Usenet doesn’t have as high of a security risk as BitTorrent.
How BitTorrent Works
In a nutshell, BitTorrent helps users share files by uploading and downloading fragments of files between users who don’t know each other. Instead of a server passing the bits and bytes of a file directly to your PC, fragments of files are sent directly from other users. Basically, it all comes down to seeders and leechers.
A seeder is a user who is hosting a file (called seeding) for others to download. On the other hand, leeching a file is synonymous with downloading a file.
In order for BitTorrent to work, there have to be some generous users who are willing to allow others to download files off their HDD for free. In turn, users who download a file can then choose to seed it, which ensures faster download times for other users who want the same file.
The whole linchpin of P2P downloads, however, is that users need to regularly seed files. Some BitTorrent clients and downloads increase your download rate the more you upload files, which incentivizes more file sharing.
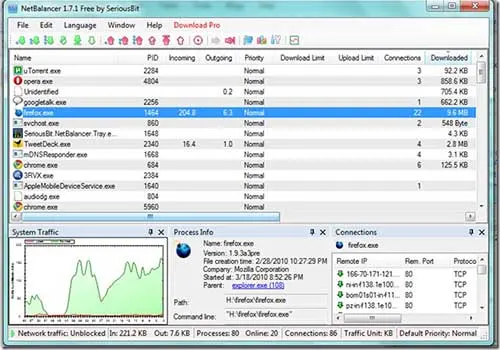
Also, note that you typically don’t download an entire file from one peer (unless there’s only one person seeding it). Instead, you connect to multiple peers and download a small fragment of the file from each peer.
Most BitTorrent clients have a graphical tool that allows you to see hosts in your swarm for any given file download. Unfortunately, BitTorrent carries some heavy risks like viruses, which we’ll discuss next.
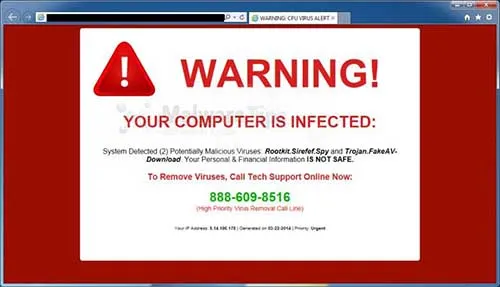
Virus and Malware Risks
As you may well know, P2P and BitTorrent downloads always carry the risk of virus infection. The problem is that you don’t always know who’s seeding a file. It could be an innocuous user just like you…or it could be a hacker who has planted malware within your download.
Hackers and attackers have long used P2P file downloads as a medium to distribute viruses, and most Bittorrent users already know this.
The good news is that there are a few easy things you can do to mitigate the threat of viruses. First and foremost, make sure that you use a good antivirus/antimalware application and scan files before you ever open them.
It’s best to use an antivirus tool that offers real-time protection to prevent some of the more opportunistic viruses from infecting your computer, even before you scan and open a file.
In addition, read the comments on a torrent before you download it. If one or more users claim it has a virus, avoid that file download like the plague it is!
Loss of Identity Risks
Another problem P2P downloaders frequently encounter is a loss of identity. When you join a swarm of seeders and leechers, your real IP address is visible to the masses. That may not sound like a big deal, but it is.
Understand that most home users typically have a single public IP address located on the WAN interface of their wireless router. If your router is set up to be remotely managed via the WAN interface, a stranger could type your public IP address into the URL bar of their web browser and attempt to log into your router remotely.
After Pandora’s box has been opened and an attacker can access your router, pandemonium can ensue. There’s a myriad of attacks a hacker could employ to capture network traffic or redirect it to one of their servers by poisoning DNS.
Furthermore, the attacker could use your IP address to pinpoint your physical location (IP addresses are distributed based on geography).
Furthermore, note that some regulatory bodies, authorities, and organizations like the RIAA have been known to join swarms in an attempt to catch infringer of copyrighted materials to file lawsuits.
Privacy is getting more important every day, but you can easily protect your privacy, anonymity, and hide your true public IP address by using a VPN tunnel. Since just about every VPN service abstains from logging users’ activities, you won’t have to worry about a loss of identity.
Instead of online strangers seeing your real IP address, they’ll only see the masked IP address that is used by the VPN server.
Bandwidth Throttling and ISP Spying
For a lot of different reasons, your ISP may also try to snoop through your data with deep packet inspection. There are a lot of complex QoS configurations that also throttle bandwidth on certain types of data and connections.
If you’ve noticed your BitTorrent downloads are extremely slow despite a fair number of seeders and a fast Internet connection, they may be choking your bandwidth.
Furthermore, some ISPs may try to spy on BitTorrent data, depending on the copyright and BitTorrent laws in your home country. Yet again, the solution is simple: just use a VPN tunnel.
A VPN tunnel hides your data with encryption, so the ISP can’t see what type of data is being transmitted. An ISP can’t classify traffic that it can’t see, so VPN tunnels are a great way at circumventing cumbersome bandwidth restrictions.
Also, I’d advise you to use a kill-switch. Many VPN providers, such as ExpressVPN, include a kill-switch in their software client. The kill-switch will pause or stop any BitTorrent downloads in the event of a tunnel disconnect.
Otherwise, the downloads would continue after the tunnel disconnected, and all that data would flow through your ISP in a visible and unencrypted format.
The Legal Risks
The last big risk with torrents is that of legality and morality. I do not advocate breaking the law. However, having said that, much of the laws surrounding BitTorrent are gray and vague. I’m sure you’ve all heard horror stories of teenagers facing prison time in the early 2000’s when copyright laws were still developing.
One of the largest problems is that there isn’t a unanimous law among different countries. In some countries, all BitTorrent downloads are explicitly criminal while in others they are tolerated for
personal use.
Whether you’re traveling or just don’t know the law in your home country, it’s worth taking a few minutes to do a little research. Laws are anything but static, and BitTorrent laws tend to change every few years.
Even though a VPN tunnel will prevent authorities from seeing that you’re using BitTorrent, you do have to ask yourself some ethical and moral questions. When in doubt, my advice is to abstain from downloading content – even if it is tempting.
Is it really worth jail time (or worse) to get your hands on the latest album or movie? I doubt it.
Conclusion
BitTorrent is a fantastic P2P technology that can be used for legal content just as easily as it can be for copyrighted materials. However, it’s fraught with security risks that could damage your computer, allow a virus to compromise your data, cause a loss of privacy, or even land you in a boatload of trouble with the authorities.
In summary, the following are the best ways to protect yourself when downloading torrents:
- Always use a VPN tunnel when downloading torrents to mask your IP address, protect your identity and anonymity, and hide data from ISPs and other authorities
- Always scan a torrent file before opening it, and use antivirus software that includes real-time protection
- Use a kill-switch to make sure your downloads only travel through the VPN tunnel
- Read comments on torrents before downloading to see if any other users got a virus from the download
- Research copyright and BitTorrent laws in your area if you are unsure
- If you don’t know the consequences, don’t click the download button
Lastly, I urge you to use good judgment and take your Internet privacy and security seriously. Even if you don’t use BitTorrent, you should still look into a VPN tunnel solution and antivirus software (such as AVG’s free antivirus) to protect yourself online. All it takes is one successful attack to cause devastating damage to your digital identity.