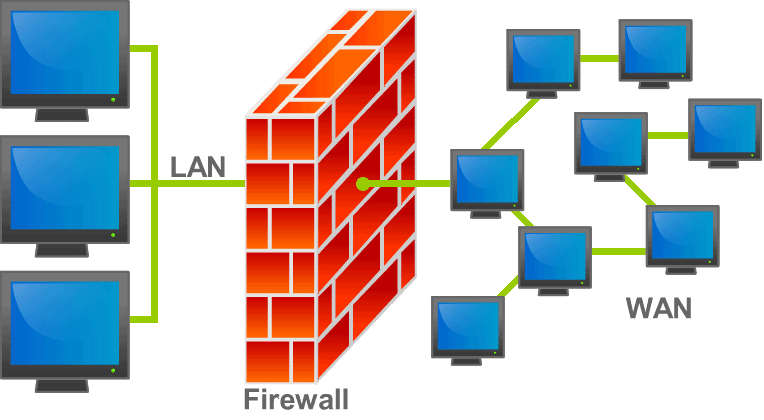
Many people, whether they are technically literate or not, have at some point in their lives come across the term “firewall.” However, to the general public, this term is shrouded in mystery and misunderstanding.
For some reason or another, Hollywood loves to throw this term around in the movies (though not always correctly). In fact, in many popular thrillers and suspense movies (like The Matrix, for example), characters commonly use phrases eluding to “hacking a firewall.”
But what the heck is a firewall and how do they increase your security? If you’re using a VPN tunnel, do you need a firewall at all since VPNs make your Internet connection more secure? We’re going to answer all of these questions, but first we need to define and understand a couple key terms including ‘firewall’ and ‘NAT.’
Firewalls Explained
It can be pretty challenging to understand what a firewall is without a previous understanding of many different Internet protocols, the OSI model, and other related topics – especially IPv4. But since this isn’t a computer networking 101 course, we’re going to assume that you know little to nothing about firewalls and don’t have the time to learn.
Let’s start by making the assertion that different types of Internet traffic are “tagged” with different numbers. We’ll go ahead and refer to these numeric tags as “ports.” So, for example, different types of networking devices will be able to treat video traffic differently from web page traffic due to its “port number.”
Firewalls then act as a sort of gatekeeper, and they can make intelligent decisions regarding how to handle these different traffic streams according to rules and policies created by an administrator. For example, you may have noticed that many VPN service providers disallow P2P traffic on their networks (usually for fear of copyright infringement laws in foreign countries).
To ensure that no P2P traffic (typically Bit Torrent downloads) traverses their servers, they simply set a rule in the firewall that blocks all incoming and outgoing P2P traffic streams.
However, this is only the core function of a firewall. They actually increase security in a variety of other ways to add extra layers of security. For example, many sophisticated firewalls can look for attack signatures – which are basically known patterns of binary code.
When they see a specific pattern flowing through the firewall, they realize that an attack is taking place and halt the traffic stream to stop it dead in its tracks.
Now take a moment to consider how crucial this is for your safety and security. Many VPN service providers use shared IP addresses. This means that the IP address you are using when you connect your VPN tunnel could have previously been used by just about anyone else on the planet.
This is a good thing because helps to protect your identity, but we have no way of knowing which servers that IP address connected to or who else on the planet became aware of the address’s existence.
All of this exposure could mean that it becomes the victim of an attack in the future…even if you’re not the intended target! Having a firewall that blocks common attack signatures (as well as a boatload of other security mechanisms like packet inspection) is essential to staying safe online.
However, that’s just a few ways that firewalls protect your security online. They also protect your anonymity and privacy through the mechanics of NAT.
NAT Explanation and NAT Firewalls
Though few providers advertise that they include NAT firewalls as part of their service (e.g. VyprVPN), just about every VPN service is going to be performing NAT. Whether or not that is performed on a firewall isn’t always clear, though, because NAT can be performed on a variety of other devices like routers, VPN concentrators – you name it.
But before we can dig into the benefits NAT firewalls offer VPN users, we first need to understand NAT.
NAT, or Network Address Translation, is a mechanism that was designed to slow down the global exhaustion of unique IP addresses (IPv4). The problem is that IP addresses are finite, and the solution was to develop a new protocol (e.g. IPv6) that would be able to supply a seemingly limitless number of addresses. With the invention of NAT, not every IP address is globally unique.
Some addresses are only valid on a local network, such as for devices connected to your local home wireless router. Every device that connects to your home router shares the same public (globally unique) IP address. But let’s take a moment to think about what this means in terms of privacy for home users.
To public servers, such as a website, it looks like a connection request was made from your home router’s public IP address. This begs the question: how does the web server know which device on your local home network made the request if they all use the same public IP address?
The answer is that the web server doesn’t know, and doesn’t have a way of tracing the connection back to an individual computer. Because the public IP address is shared with other devices, there’s no way of knowing where the request originated from.
However, understand that your home router does keep a table that matches local network hosts and the corresponding connections they made. Essentially, the bottom line is that only your home router has a way of tracing the IP addresses and connection requests made by hosts via its NAT table.
NAT Firewalls and Privacy Policies
Clearly, this helps to provide an extra layer of anonymity. Let’s take things one step further, however, and consider how NAT adds anonymity with a VPN service. Your VPN service provider’s devices are going to keep NAT tables that translate your IP address with one that they already own.
To every website and web server you connect to, it appears that the VPN server is making the request. Therefore, public web servers are blind to your true IP address. You might be concerned that your VPN service provider keeps records of metadata – and it’s true…just about every service does.
However, any good VPN service isn’t going to share that information with external third parties. This is where doing a bit of research is paramount to protecting your privacy. All you have to do is check out the privacy policy of a prospective VPN service, and you’ll most often find that they don’t log user data or share their NAT records unless coerced by law enforcement.
Some provider even claims that they delete these tables, logs, and metadata within 24 hours to eliminate any possible paper trail.
In Summary
While we already know that VPN services perform NAT, we don’t always know which devices the NAT is performed on.
In summary, the following are the added benefits of NAT firewalls:
- Blocks unwanted incoming connection attempts
- Helps add security with packet inspection and searching for attack signatures, viruses, etc.
- Protects any device connected to the VPN tunnel
- Adds an extra layer of anonymity through NAT
- Helps reduce spam and malware
- Some even include port forwarding features, which send traffic on ports that aren’t standard to help disguise the traffic and data