Network devices, web administrators and antivirus applications make a regular habit of blocking IP addresses.
Whether your domain name, true public IP address, or VPN/proxy address has been blocked (regardless of the service you’re trying to access), you may not have known that there are some workarounds.
The age old solution was to employ a technique called IP address masking, whereby a proxy server or VPN server would essentially act as you personal data broker and allow you to “borrow” it’s public IP address.
But these days, security has advanced to a level that wasn’t even fathomable a decade ago. There are umpteen ways for a network device or website to block your computer from establishing a connection wish a web server and exchanging information.
And I don’t care what data you’re trying to exchange; the bottom line is that Internet and web restrictions are a royal pain in the rear end.
The good news is that there are plenty of ways to circumvent these types of restrictions. If you’re just trying to unblock geo-restricted content, then I recommend a VPN tunnel as your first line of attack.
But today we’re going to be taking a look at the bigger picture by identifying other common restrictions and show you how to get around them. To start, let’s take a look at various ways that computers and resources are blocked.
Different Blocking Methods
Sometimes people erroneously think that their IP address has been blocked, when in reality, other TCP/IP data has been detected and filtered.
Web administrators, network engineers, and governmental authorities have a lot of tools in their tool belts when it comes to shutting down connections.
I certainly don’t have enough time to create a comprehensive list of all the ways Internet connections are controlled. However, from the average user’s point of view, there are only five main restrictions that matter the most.
The following are a few of the most common ways to block IP addresses:
- Domain-Level Filters
- Geo-Restrictions
- Blacklist of Selected Addresses
- Meta-Data in the TCP/IP Packet Header
- TCP/IP Ports
So let’s take a closer look at each of these methods and talk about their individual solutions.
1. Domain-Level Filters
Domain-Level filters are extremely common, and are used in a variety of ways. Not only are these types of filters used by governmental agencies around the world to block access to websites, they are also used frequently on a personal basis.
I’ve seen tons of consumer grade wireless routers and parental control software that comes with domain-level filter features. The user simply needs to enter a specific page URL or domain name, and the website is blocked to the local users.
Interestingly enough, I’ve seen some of these filters only block the DNS request, so let’s run through the process of DNS in a nutshell.
Essentially, domain-level filters block DNS requests so your computer can’t look up the IP address of the server it wants to connect to.
For instance, you may want to search for www.examplewebsite.com, but your DNS server may intentionally prohibit a resolution of that domain.
What to do to circumvent restrictions:
In these cases, using a VPN or proxy connection will easily overcome the domain-level filter. VPNs are the recommended solution because they add encryption to your connection, but note that there are three main solutions, as follow:
- Depending upon how the restriction was setup, changing your DNS server may allow you to circumvent restrictions
- Use a VPN tunnel (recommended)
- Use a SmartDNS service or proxy server
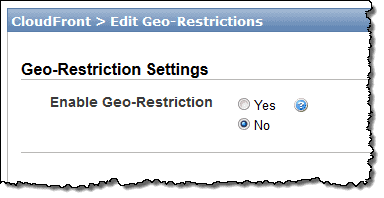
2. Geo-Restrictions
Geo-restrictions are really common these days, especially in the realm of sports and content that networks want to protect. The problem with international content distribution is that licensing and copyright law is ridiculously complex.
To protect legal and financial interests, many on-demand streaming content providers and media websites block access to foreign IP addresses.
You see, IP addresses are globally distributed in a structured way that makes it possible to know where a user is connected to the Internet.
IP address structure and distribution was originally performed by IANA (Internet Assigned Numbers Authority) for technical reasons that made it possible for data to be more efficiently routed.
The net effect, however, is that a USA IP address looks very different from a French IP address, if you know which blocks are distributed to which parts of the world.
Even if you don’t, a quick Google search will show you where an IP address is physically located. Also, note that whenever you connect to a website, it knows where you are physically located in the world if you are connecting with your true IP address.
It’s ridiculously easy for a content server to see which country you’re in, and to then permit or deny you from accessing content.
What to do to circumvent restrictions:
These are perhaps the easiest restrictions to circumvent (with the exception of blacklisted IP addresses, as we’ll discuss next). The solution is to employ IP address masking, as we did with domain level filters.
The following outline the best ways to circumvent geo-restrictions:
- Use a VPN tunnel to hide your real IP address (recommended)
- Use a proxy server (beware that proxy connections lack encryption)
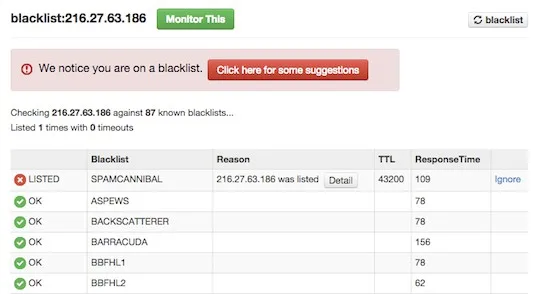
3. Blacklist of Selected IP Addresses
Sometimes web servers and Internet resources cherry pick lists and groups of IP addresses that they want to block. Often these lists of IP addresses are shared with public development groups, but they change very quickly.
You see, IP addresses change hands a lot and get new owners, a bit like how an apartment will see many tenants in its lifetime.
For services like Hulu, this is a big problem because it’s like playing a game of whack-a-mole. Once Hulu finds all or most of a provider’s IP addresses (they likely never find all of them), that list needs to be continually updated like a living document.
The VPN provider may bring new servers online that have new addresses, or lease a larger block of IP addresses from IANA or their service provider.
It does admittedly suck when you connect to a VPN service to circumvent geo-restrictions, only to find that the service is blocking your VPN service provider‘s IP addresses too!
But fortunately, you can get around these blacklisted IP addresses using several different methods.
What to do to circumvent restrictions:
- Try disconnecting and reconnecting to lease a new IP address from the same location or VPN server
- Connect to a VPN server hosted within the same country/region, though in a different city (many VPN providers host multiple server locations in a single country)
- Research all of the countries where the desired content is available, and try connecting a VPN server in another valid country
- Try a trusted proxy server connection (this would be my last resort…I detest proxy servers that lack encryption)
If you’re having trouble, I’d recommend refreshing a page that will show you your masked IP address. Just Google “what is my IP” and you’ll get tons of websites that will display that information for you.
That way you’ll know if you’re really getting a new IP address, or just trying to connect to a server from the same address every time.
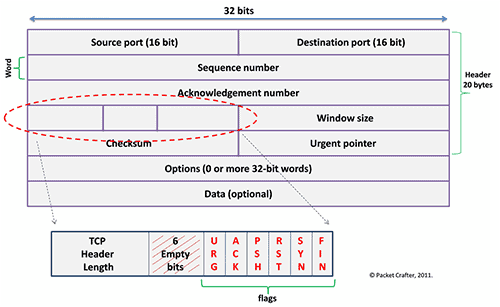
4. Meta-Data in the TCP/IP Packet Header
Sometimes various networks and governments restrict the use of VPN tunnels.
Right now, China is the most infamous banner of VPN technologies, and the Great Firewall of China does its best to shut down VPN connections through various methods and technologies.
One of those methods, however, is called Deep Packet Inspection, or DPI.
DPI is a packet filtering technique that can analyze the TCP/IP packet header and payload to look for different metrics and qualifiers, and then permit, deny, or rate limit different types of traffic.
DPI can also be used to scan for viruses, and to block traffic that looks suspicious. Unfortunately, it can also be used to identify whether or not a TCP/IP packet contains data that’s being sent through a VPN tunnel.
A rare few providers, such as VyprVPN, have features specifically designed to prevent Deep Packet Inspection. This is great for circumventing network restrictions that would block the VPN tunnel connection process in the first place.
Sometimes when DPI (and similar techniques) block a VPN connection, the end user thinks, “Oh no, they must have blocked my IP address,” or “Huh, maybe the VPN server is down or busy.”
In reality, DPI is blocking the connection, but providers like VyprVPN can still get through because of their proprietary algorithms.
What to do to circumvent restrictions:
If you suspect that your ISP, government, or network administrator is blocking the use of VPN tunnels, your best bet is to try a service like VyprVPN that can disguise your tunnel with special features.
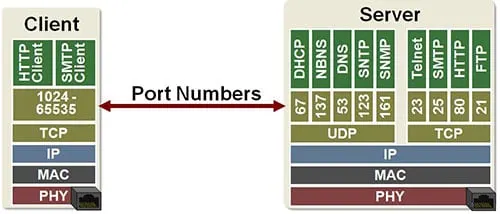
5. TCP/IP Ports
You may have already heard the term “ports,” either because you’ve had to make configurations that concern ports on your firewall or because the term is bandied about in just about every film that involves hacking, computers, and suspense.
But whether you have a deep knowledge of TCP/IP ports or not, for the sake of this discussion, just know that a port is simply a numerical identifier that tags different types of traffic.
A network engineer could tag different types of traffic with different port numbers to help network devices and end users treat types of traffic differently by default.
For instance, all voice traffic (VoIP) could be assigned its own unique number while HTTP web traffic could be assigned a different identifier.
This helps separate traffic types into groups so that traffic can be routed, managed, permitted, denied, expedited, or queued according to its needs.
The following examples highlight some of the most common TCP/IP ports:
- Port 80 – HTTP (basic web page traffic in a browser)
- Port 443 – HTTPS/SSL
- Port 20/21 – FTP (File Transfer Protocol)
- Port 53 – DNS
- Port 500 – IKE (Internet Key Exchange)
- Port 1723 – PPTP
There are thousands of different port numbers used for every imaginable purpose, but know that the first thousand ports (0-1024) are within the “well-known” range and contain all the common everyday protocols.
You should also know that it’s common practice to block different protocols due to local network policy, national data laws, security, and other similar reasons.
For example, if I lived in a country where VPNs were banned, it might be national policy for ISPs and public networks to completely block ports 500 and 1723 to prevent users from establishing VPN tunnels using PPTP or IKE connections.
What to do to circumvent restrictions:
The typical solution is to simply send that data to different port to disguise its identity. For instance, if my VPN tunnel used IKE for negotiation but my local network blocks port 500, I could simply send that data to another port, assuming my software client and the VPN server allow me to change that setting.
By setting the server and client to send that IKE traffic over port 443 instead of port 500, it would look like simple HTTPS traffic to any eavesdroppers or a firewall.
Final Thoughts
By and large, most people don’t have trouble establishing a VPN connection or accessing streaming on-demand content through a VPN tunnel. But once in a while, your IP address or VPN connection may get blocked.
In these cases, remember to use the aforementioned troubleshooting methods to circumvent any restrictions you may encounter.